According to the report in (INSTRUMENTS, 2020), the vulnerabilities facing BLE 5.0 is deemed very high and more so due to the various benefits and capabilities of Bluetooth 5.0 technology, which has made it a primary communication medium of choice for connected devices, as opposed to Wi-Fi. The increased bandwidth and connection distance has been a source of vulnerability, because attackers can access Bluetooth connections from a long distance away, and with fast data transfer speed, can wreak havoc without notice. According to NIST report, (NIST, 2012) common areas of vulnerabilities in traditional Bluetooth 5.0 are as follows:
- Lack of end to end security
- No user authentication
- Insecure storage of link keys
- Discoverable devices
The lack of end to end security is a major vulnerability of the traditional BLE system. The current system implements individual link encryption, with message decryption at intermediate points on the communication link that could lead to man in the middle attacks (MITM), also the absence of application and user level authentication as a default in the Bluetooth specification is also an area of vulnerability, as the currently offered device level authentication isn’t sufficient nor impervious to malicious attacks, possibility of data corruption during improper synchronization, potential for loss of data stored on an IIoT device if stolen are all very critical.
Man in the middle (MITM) attacks can be mitigated by the deployment of user input passkeys, although passkey linking isn’t applicable for applications without a keypad or a display, passkeys are also not well suited for passive eavesdropping attacks. Passive eavesdropping attacks are attacks which are a little different from man in middle attacks, in that the eavesdropper doesn’t intend to change or impersonate data; rather he/she sits idly, while gathering information. (INSTRUMENTS, 2020) Surmises that at least 80% of all Bluetooth enabled smart devices are vulnerable to man in the middle attacks (MITM).
Data transmission over the Bluetooth 5.0 uses AES-CCM encryption, where this encryption takes place in the Bluetooth controller. Bluetooth low energy encryption security modes are of two types; namely the LE security mode 1 and the LE security mode 2 as shown in fig 3.
LE security mode 1 has four security levels, namely the no security (no authentication, no encryption mode), the unauthenticated pairing with encryption, the authenticated pairing with encryption and lastly the Authenticated LE Secure Connections pairing with encryption using a 128-bit strength encryption key. Where, each security level satisfies the requirements for the level below it.
LE security modes /levels and their associated characteristics are depicted in fig 4.
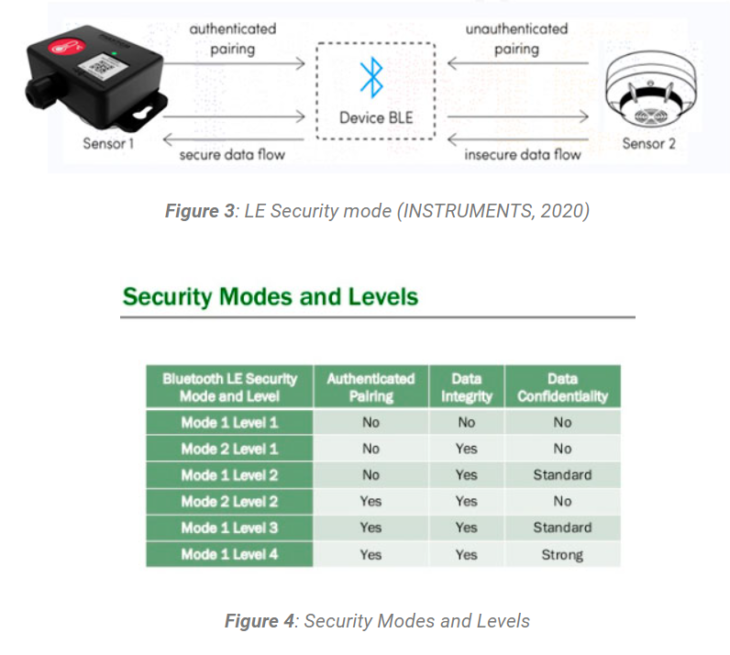
In LE security mode 2, it consists of two security levels, namely the unauthenticated pairing with data signing and the authenticated pairing with data signing. It is mainly used for transferring data between two devices on an unencrypted connection.
Elliptic Curve Diffie-Helman cryptography is used for key exchange in Bluetooth LE Secure Connections, according to the Bluetooth Specification Version 5.0. This helps protect against passive eavesdropping but may be susceptible to Man in the Middle (MITM) attacks. However to prevent that, random passkey generation is recommended each time pairing is initiated, where the ‘master’ and ‘slave’ device will each generate a 128-bit random number, which will serve as a temporary key (TK).